Secret Management
The Secret Management setting gives facility to prevent the database-related or any other sensitive/confidential information from getting exposed. In Secret Management Settings the Admin configures the Key of the Sensitive data but the actual value is saved in Kubernetes as Environmental Variable by the DevOps Team.
Steps to Add Secret Key
Click on the Secret Management icon from the Configurations section provided in the Admin panel.
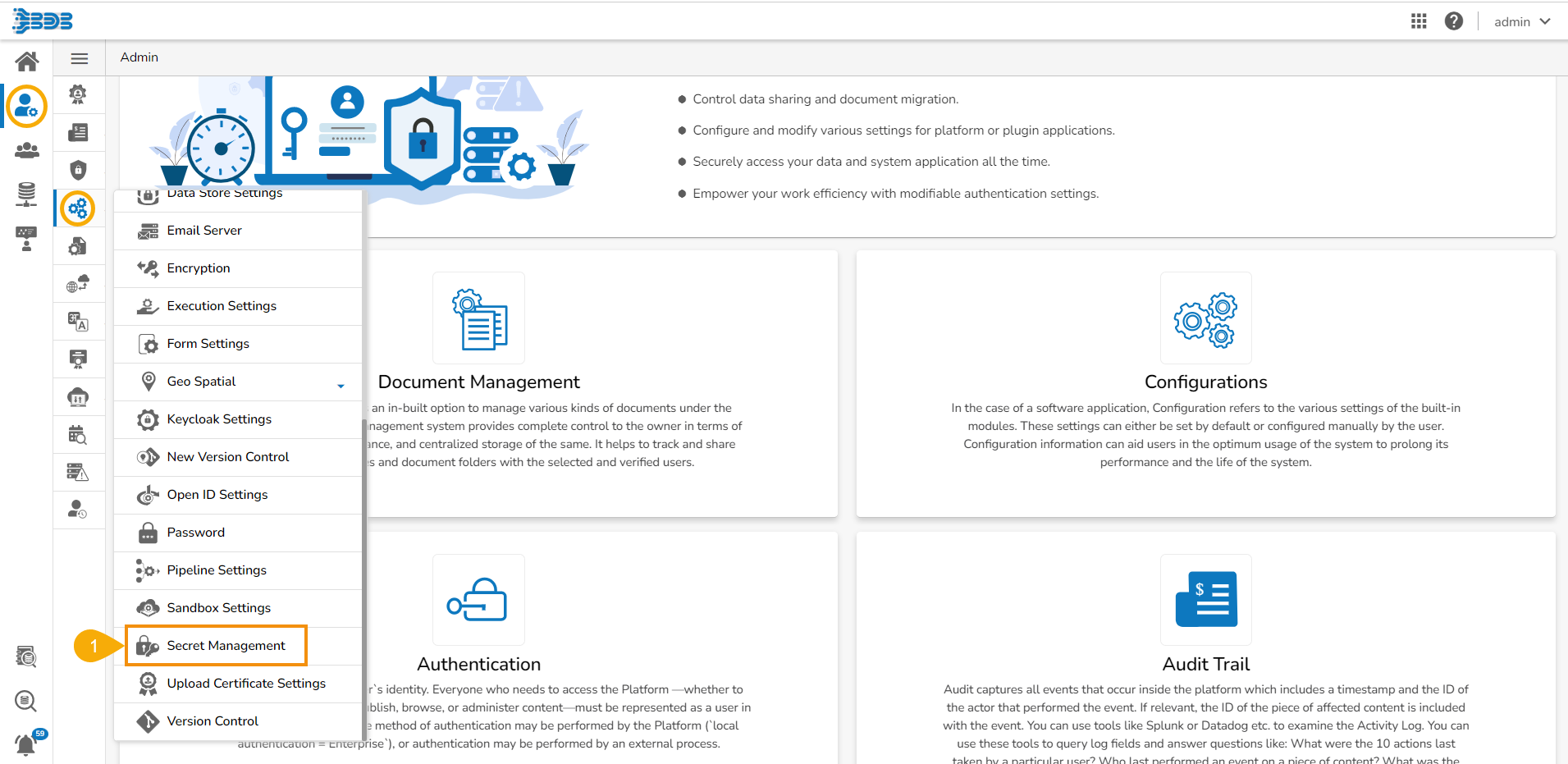
The Secret Management page opens.
Click the New option to add a new secret.
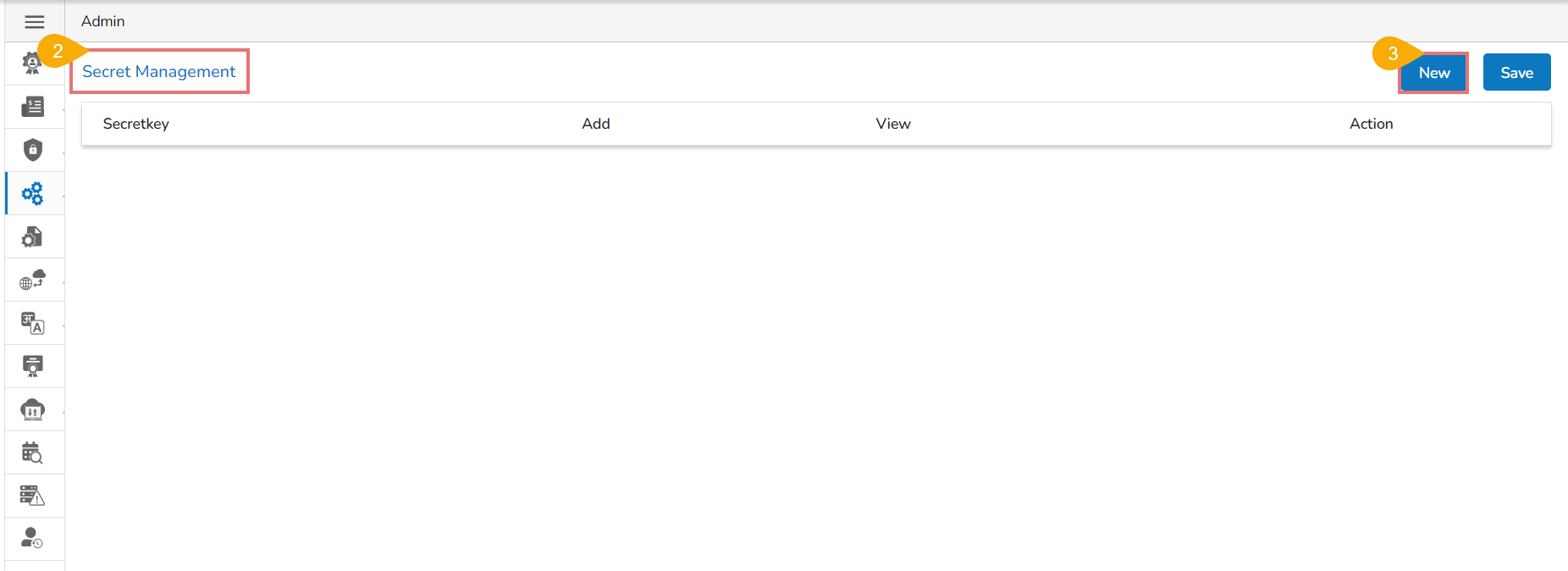
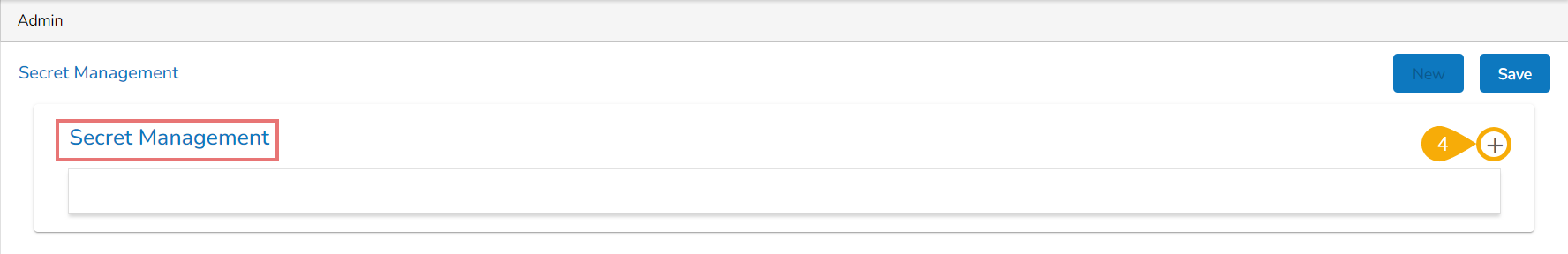
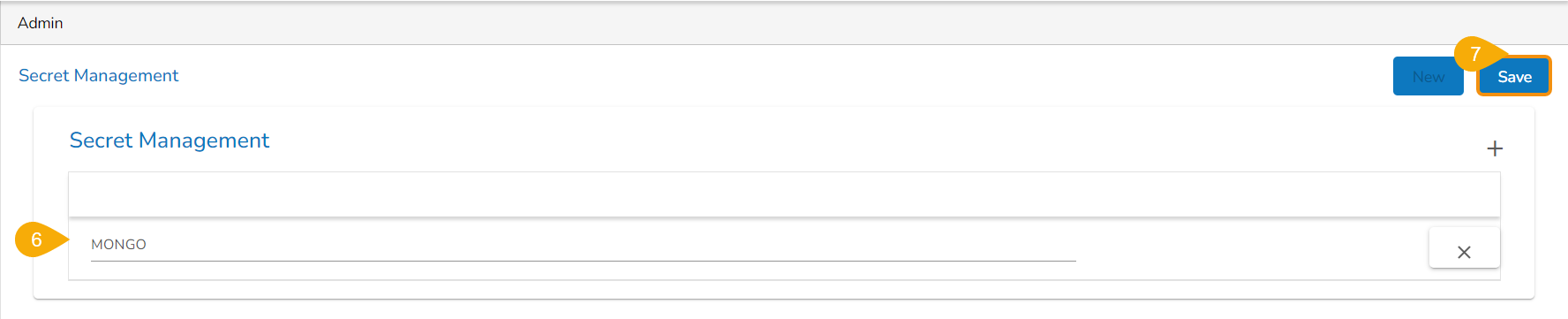
Click the Add New Field icon for the Secret Management option.
An option to add the Secret Key appears as shown in the below image:
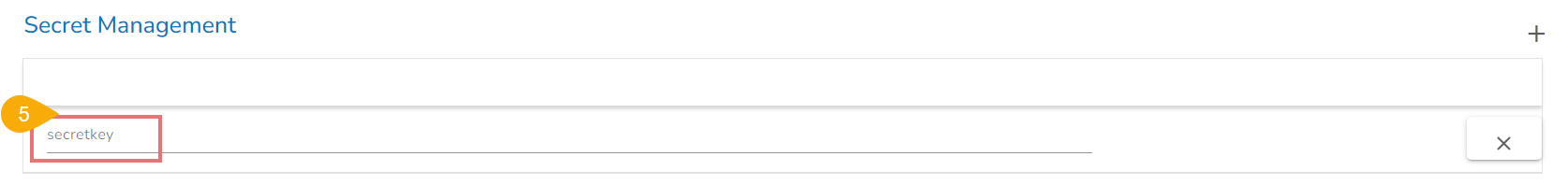
Provide the Secret Key in the given space.
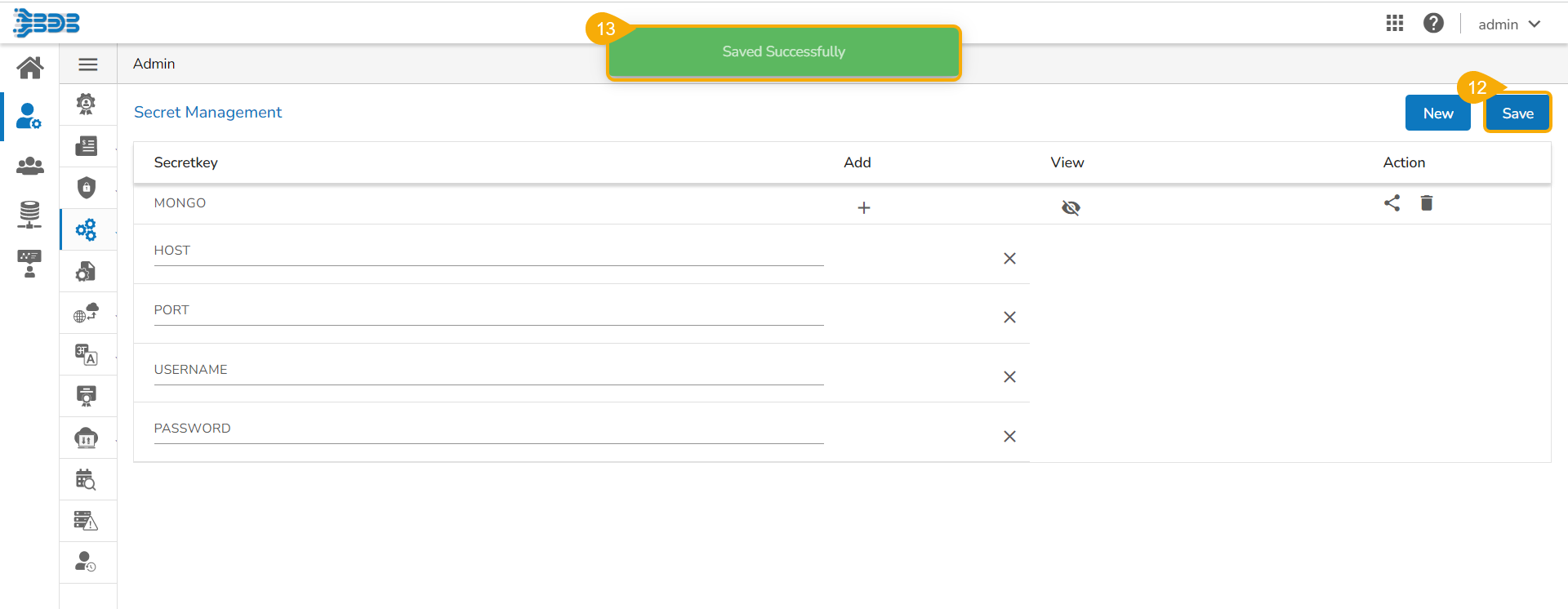
Click the Save option.
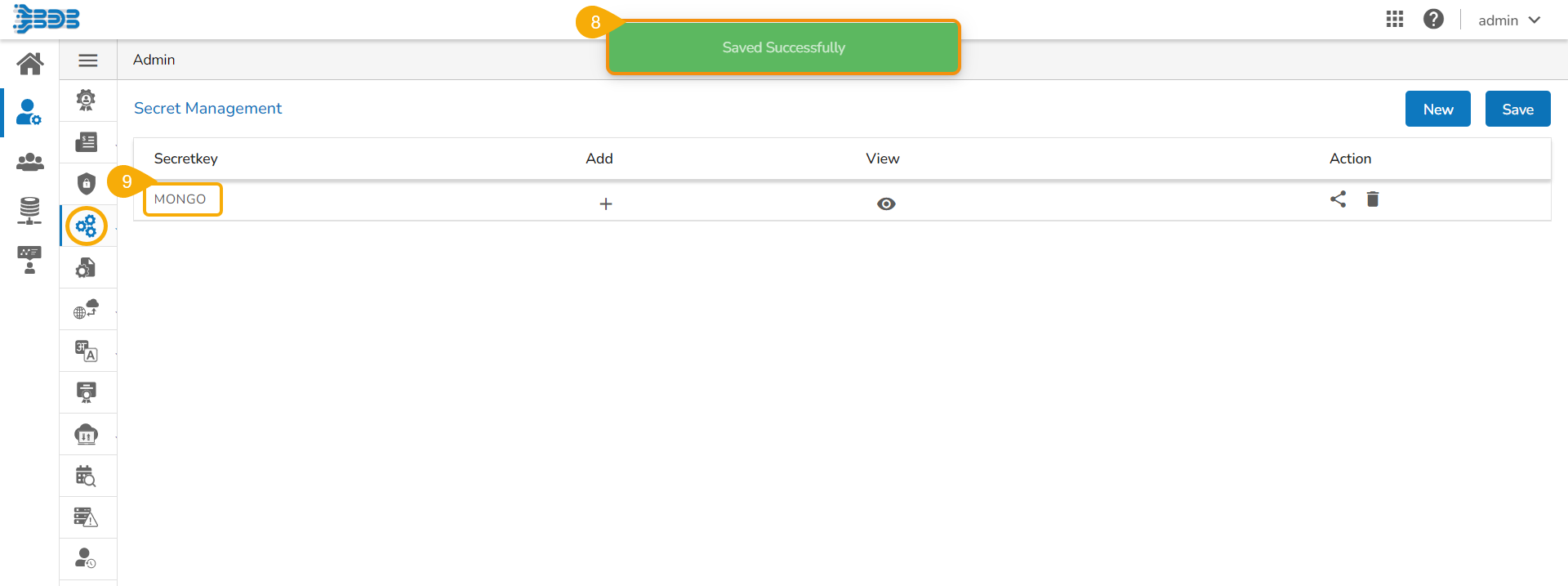
A confirmation message appears.
The secret key will be saved and displayed in the list.
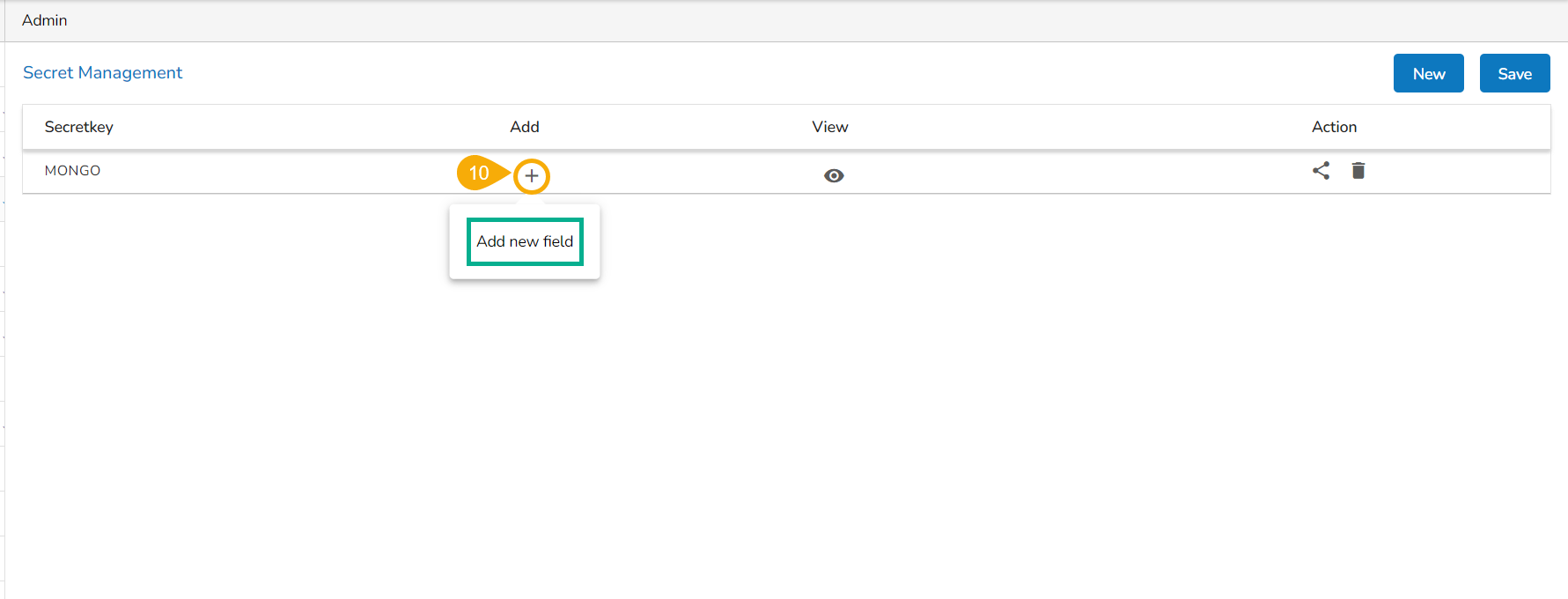
To add a new field click on the Add + icon provided for the Secret key.
Add multiple fields like Port, Host, Username, Password, etc. depending upon the selected DB.
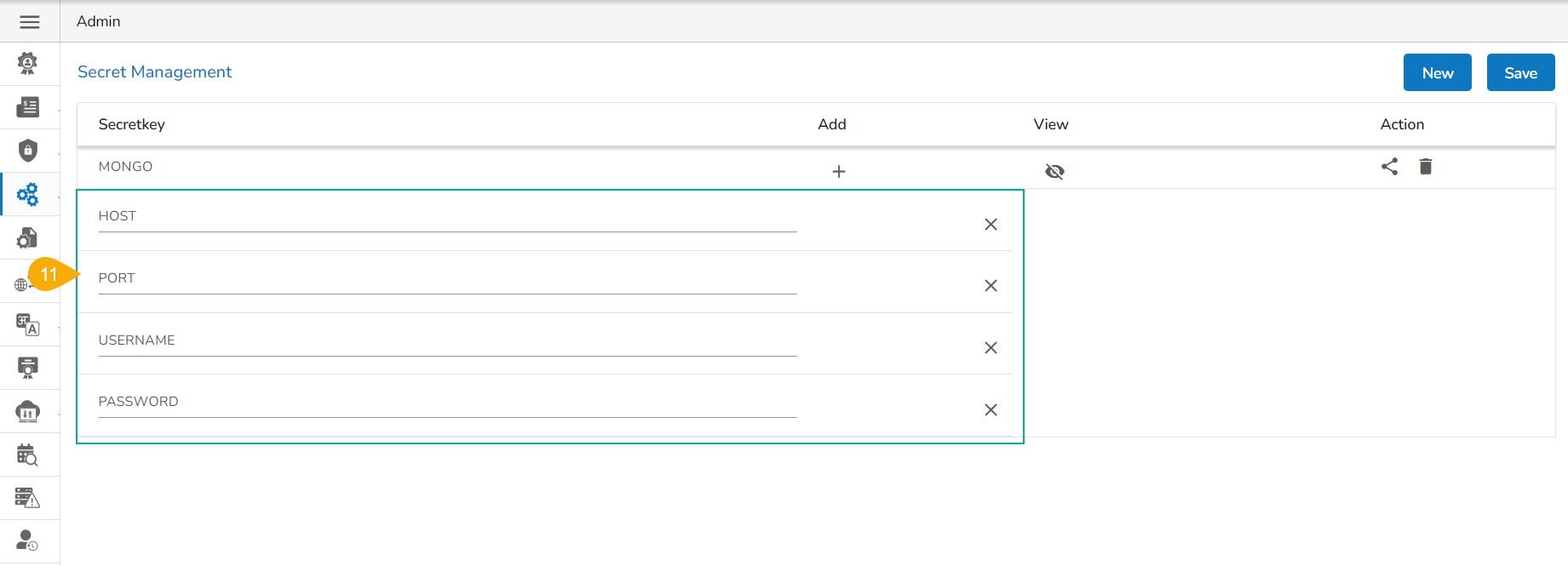
Once all the required fields are added, click the Save option.
A confirmation message appears to ensure that all the inserted fields are saved.
Please Note:
Click the View
 icon to display all the added fields.
icon to display all the added fields.Click the Delete
 icon to remove the added Secret key.
icon to remove the added Secret key.Click the Close
 icon to remove an added field.
icon to remove an added field.
Steps to Share a Secret Key
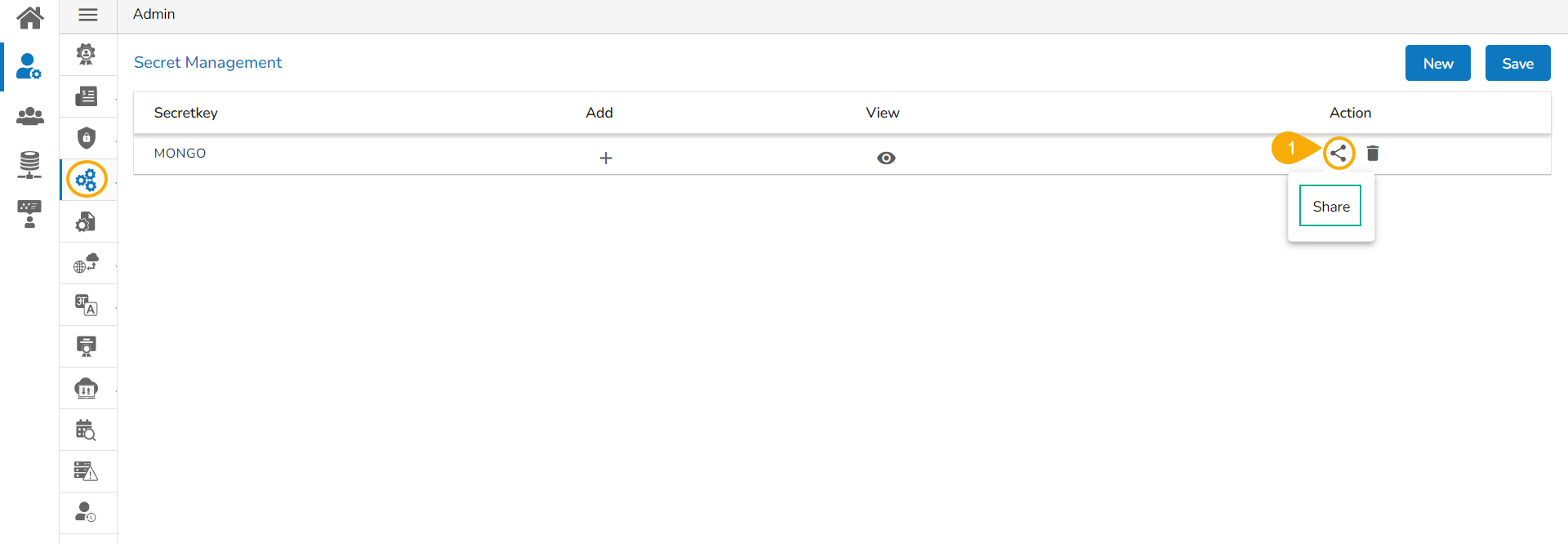
Once Admin has configured the settings, it is possible to share it to a user/user group to use the encrypted secret keys. Click the Share ![]() icon provided next to a saved Secret Key to share it.
icon provided next to a saved Secret Key to share it.
Click the Share icon for a saved Secret Key.
The Share Secret Key window opens.
Select the USER or USER GROUP option to list the users (Use the EXCLUDE USER to exclude the user from the right to access a shared Secret Key).
Select User(s)/User Group(s) from the list.
Use arrow to move the selected user(s) and user group(s) to the right side box.

Once the selected user(s) and user group(s) appear in the right side box.
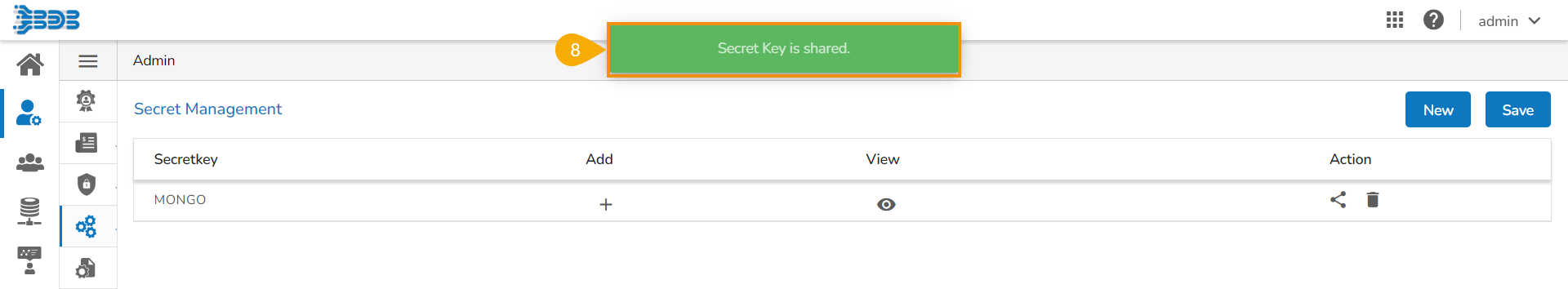
Click the Save option.

A confirmation message appears and the Secret Key gets shared to the selected user(s) or user group(s).
Please Note:
Admins must request DevOps to add keys and values in Kubernetes, adhering to Kubernetes naming conventions (Use hyphen or underscore, special characters are restricted) .
Admins must share these secret keys with relevant users/user groups for access.
Once configured and shared to respected users and user groups these keys can be utilized across platform modules.
Last updated